For years, industry experts have been advising that visibility should be the starting point of an OT security roadmap. You can’t fix what you can’t see, right? It’s why so many organizations invest in OT visibility tools as their first step.
But too often, they quickly realize a hard truth: deploying a visibility platform by itself, even one in the top right corner of Gartner’s Magic Quadrant doesn’t get them much closer to their ultimate goal. Did they pick the wrong tool? Not at all.

An OT visibility tool alone won’t complete your security roadmap, and more importantly, it won’t provide all the protection your OT environment needs.
The fundamental issue? Visibility alone isn’t enough. If you’re not patching or only patching once a year, it will likely confirm what you already suspect: you have lots of vulnerabilities.
Many teams find themselves stuck at stage one of their roadmap, unable to move forward due to the cost, complexity, and operational downtime required for the next steps. They can see the risks clearly—but lack the means to act on them.
OT Visibility Isn’t The Ultimate Goal— Actual Protection Is
While visibility tools help you see risks and (in most areas) monitor network traffic, they aren’t designed to block attackers, prevent unauthorized lateral movement, or protect legacy systems from unpatchable vulnerabilities.
The actual security measures defined on your roadmap are very likely:
-
- Network data encryption: Secure OT data in motion with high-speed, low-latency encryption that supports time-sensitive industrial protocols.
- Micro-segmentation: Break down your network into isolated segments to prevent threat propagation and reduce your attack surface.
- Asset cloaking: Hide high-value systems and vulnerable devices from attackers, rendering them invisible to reconnaissance and discovery tools.
- Granular access control: Enforce Zero Trust policies that limit access by role, user, or device, and require multi-factor authentication.
These aren’t nice to have upgrades you consider after achieving visibility—they’re the very outcomes you’re expected to deliver. They represent the essential protections required to mitigate security threats, close critical gaps, and keep attackers at bay.
You already know these measures are essential. Your security team might have even mapped out a detailed plan for implementation, including network re-architecting, re-IPing, and worst of all—the expected days of planned downtime. But even if your security budget had the elasticity to include these technical costs, your production schedules—or if you are a utility, your customers’ need for uninterrupted service—simply won’t allow for this loss of uptime and production. It’s a non-starter.
The result? You’re left with a visibility tool that provides important insights into the deeper levels of your OT environment—but has uncovered (or confirmed) a long list of critial of vulnerabilities that remain unprotected.
Go Beyond OT Visibility and Add Actual Protection Without the Pain
What if you could actually protect your OT assets—without ripping and replacing infrastructure, shutting down production lines, or blowing past your security budget?
That’s where the Opscura OT Protection Platform comes in.
Our next-generation solution goes beyond monitoring to actively defending your environment by integrating key protections like encryption, segmentation, and cloaking. It’s a unified, drop-in platform designed to work within your existing infrastructure, requiring no re-architecting or downtime. Even better, it integrates seamlessly with all leading visibility tools, instantly transforming them from passive observers into powerful enablers of protection.
Unlock the Value of Your Visibility Tool by Adding Actual Protection
As we’ve established, visibility is only the starting point. The real challenge is taking action.
If your company already invested in visibility, we have good news—we’re already partnered with visibility and network infrastructure leaders to help you take your OT security to the next level. Our seamless integration ensures that you can go beyond monitoring and start actively protecting your critical assets without adding complexity.
Not working with these best-in-class visibility tools yet? No problem. Whether you’re starting from scratch or still building out your OT security stack, Opscura adds real protection with no re-IPing, no infrastructure changes, and no downtime. And if a visibility solution is in your roadmap, Opscura doesn’t just prepare your environment—it accelerates the tool’s deployment, value, and ROI from day one.
How Opscura Takes Your OT Security Further
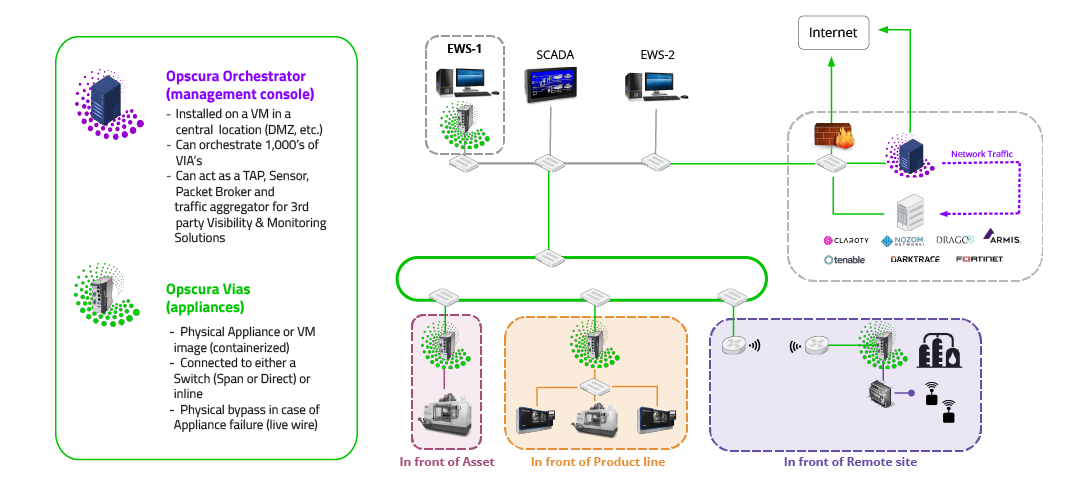
Opscura’s OT Security solution integrates with your existing security monitoring and threat management systems, ensuring traffic from each asset is labeled and properly monitored. Unlike traditional approaches that require multiple tools across different locations, Opscura simplifies security with a flexible deployment model. Whether in front of individual assets, entire production lines and zones, or across an entire facility, Opscura enhances OT visibility with actual protection—deployed with a drop-in solution that requires no disruption or downtime.
Opscura operates at OSI Layer 2, fully compatible with any Ethernet protocol. The solution applies crypto-segmentation, encrypting and isolating traffic between assets or zones while keeping critical communications secure and hidden from adversaries.
With Opscura, you go beyond passive monitoring. Our Orchestrator and Vias enable proactive protection through segmentation and encryption, ensuring that your visibility tools don’t just detect threats—they help stop them. Vias function as an all-in-one TAP, sensor, traffic broker, and aggregator, feeding critical OT data into your existing monitoring stack while cloaking high-value systems and reducing your attack surface. This approach strengthens your security posture while eliminating unnecessary complexity and cost.
Do More with Fewer Devices
What sets Opscura apart from traditional TAPs or sensor providers (such a Garland or Gigamon to name two) is our ability to deliver comprehensive OT security, the full range of desired OT security outcomes, with fewer devices and less complexity. Traditional OT security solutions often require multiple tools such as packet brokers, aggregators or firewalls, complex integrations, and high operational costs.
Opscura’s OT Security Protection Platform eliminates these challenges by consolidating multiple security functions into our Vias, a single, easy-to-deploy solution. Vias are available as physical or virtual appliances, with built-in bypass functionality to ensure fail-safe operation in critical environments.
With Opscura, you can:
-
- Segment your network and assets: Define conduits by asset, user, or session to enforce zone-based access control and contain threats at the source.
- Encrypt your network traffic: Use high-speed low-latency (<1ms) encryption to secure time-sensitive OT protocols—without compromising performance.
- Cloak critical assets: Hide legacy systems and vulnerable assets from attackers who may be conducting network discovery.
- Micro-segment your network: Implement Zero Trust principles with authentication by zone and role-based access policies—fully integrated with your SIEM and IDS.
By doing more with fewer tools, Opscura simplifies OT security architecture, lowers costs, and reduces deployment time—while increasing protection. It’s an intuitive, scalable solution that addresses modern OT security challenges without disrupting operations.
Take Control of Your OT Security Today
Opscura enhances your existing security tools and provides full OT network visibility. Our flexible deployment scales with your needs, ensuring your security evolves with your OT roadmap. Beyond visibility, we offer protection through segmentation and encryption—without downtime.
Whether you’re starting from scratch or building on existing tools, Opscura speeds up your security roadmap and optimizes your investment.
Deploy anywhere. See everything. Protect it all.
Learn how we can help protect your OT network and accelerate your security journey—without the complexity and cost of traditional solutions.